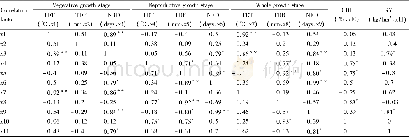
《Table 2 The relationship between Charlie’s, Uj’s, and Bob’s measurement results.》
 提示:宽带有限、当前游客访问压缩模式
提示:宽带有限、当前游客访问压缩模式
本系列图表出处文件名:随高清版一同展现
《A Quantum Multi-Proxy Blind Signature Scheme Based on Entangled Four-Qubit Cluster State》
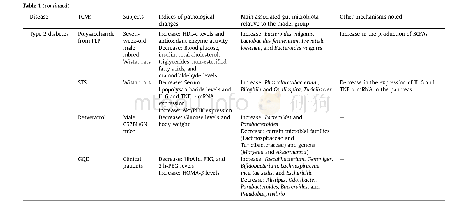
(iii) To guarantee the security of the quantum channel,Charlie and Ujarrange eavesdropping checks.On the one hand,Charlie chooses T N-tn groups of particle 4randomly,remembers the positions and performs a measurement with the basis,then Charlie publishes the positions.According to Charlie’s published positions,Ujperforms measurement on the particles(1,3)with the basis,Bob performs measurement on the particle 2 with the basis.After that,Charlie,Ujand Bob all declare their measurement outcomes.Here,the declared order of them should be random.If their measurement outcomes satisfy the relationship in Table 2or error rate is less than the threshold value,the quantum channel is safe.Otherwise,they give up this process.On the other hand,Ujalso arranges eavesdropping check by randomly choosing Q-n EPR pairs to ensure the safety of the quantum channel between Ujand Alice.This process is similar to the above mentioned,we do not repeat the details.
| 图表编号 | XD008360600 严禁用于非法目的 |
|---|---|
| 绘制时间 | 2018.07.01 |
| 作者 | 牛旭峰、张建中、谢淑翠 |
| 绘制单位 | College of Mathematics and Information Science, Shaanxi Normal University、College of Mathematics and Information Science, Shaanxi Normal University、School of Science, Xi'an University of Posts and Telecommunications |
| 更多格式 | 高清、无水印(增值服务) |