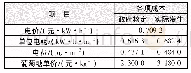
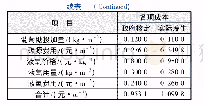
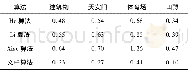
《Table 1 Time consumption operations》
 提示:宽带有限、当前游客访问压缩模式
提示:宽带有限、当前游客访问压缩模式
本系列图表出处文件名:随高清版一同展现
《Fast Confidentiality-Preserving Authentication for Vehicular Ad Hoc Networks》
Accordingly,the estimated time is exhibited in Table 1,where TSMis scalar multiplication,TPAis point addition,TBPis bilinear pairing,and TMPHis map-topoint special hash function.Vi’s side signature generation would use almost 0.39 ms and RSU’s would use0.78 ms for verification.If any simultaneous multiplication method would be employed as explained before,RSU’s also uses 0.39 ms of course.
| 图表编号 | XD0042857400 严禁用于非法目的 |
|---|---|
| 绘制时间 | 2019.02.01 |
| 作者 | MIRZAEE Siavash、蒋乐天 |
| 绘制单位 | Department of Electronic Engineering, Shanghai Jiao Tong University、Department of Electronic Engineering, Shanghai Jiao Tong University |
| 更多格式 | 高清、无水印(增值服务) |