《Tab.1 Attack strategy》
 提示:宽带有限、当前游客访问压缩模式
提示:宽带有限、当前游客访问压缩模式
本系列图表出处文件名:随高清版一同展现
《一种对抗协作频谱感知中拜占庭攻击的博弈论方法(英文)》
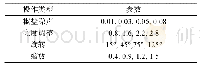
The attacker launches IA w hile the channel is being used by the PU.The FC's final decision is also accurate,and the attacker has to leave due to no benefits,and such a situation is denoted as IA-L.When the channel is unused,the attacker w ith IA can access it as w ell as the reliable SUs for transmitting data,w hich is denoted as IA-nO.After all SUs have sensed the active or inactive PU,since the attacker implements NA and operates like reliable SUs,the final decision is also idle or busy;therefore,both the attacker and reliable SUs access the unused channel or sw itch to another channel after the sensing slot.These tw o situations are respectively denoted as NA-L and NA-nO.Notably,NA-nO means no difference betw een the unintentional attacker and reliable SUs.Through the above analyses,the attack strategy is listed in Tab.1
| 图表编号 | XD0015630300 严禁用于非法目的 |
|---|---|
| 绘制时间 | 2018.12.01 |
| 作者 | 吴俊、宋铁成、于越、胡静 |
| 绘制单位 | 东南大学信息科学与工程学院、东南大学信息科学与工程学院、东南大学信息科学与工程学院、东南大学信息科学与工程学院 |
| 更多格式 | 高清、无水印(增值服务) |