《Table 3 Operations of the victims》
 提示:宽带有限、当前游客访问压缩模式
提示:宽带有限、当前游客访问压缩模式
本系列图表出处文件名:随高清版一同展现
《OvBNN authentication based on cooperative signature for wireless sensor networks》
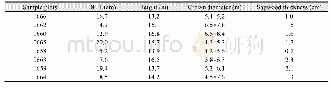
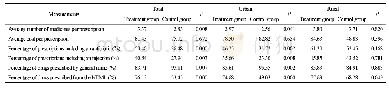
All these three intermediate results being sent to the neighbors will make the network vulnerable to the following attacks.Table 2 and Table 3 show the actions performed by the attackers and the victims.
| 图表编号 | XD0020602000 严禁用于非法目的 |
|---|---|
| 绘制时间 | 2018.09.01 |
| 作者 | 秦丹阳、Zhang Yan、Ma Jingya、Ji Ping |
| 绘制单位 | Key Lab of Electronic and Communication Engineering,Heilongjiang University、Key Lab of Electronic and Communication Engineering,Heilongjiang University、Key Lab of Electronic and Communication Engineering,Heilongjiang University、Key Lab of Electronic and C |
| 更多格式 | 高清、无水印(增值服务) |