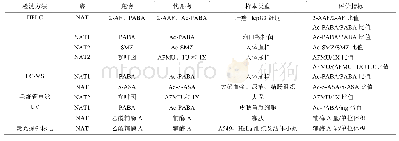
《Tab.1 Overview of different detection methods》
 提示:宽带有限、当前游客访问压缩模式
提示:宽带有限、当前游客访问压缩模式
本系列图表出处文件名:随高清版一同展现
《基于网络行为特征与Dezert-Smarandache理论的P2P僵尸网络检测(英文)》
To verify the accuracy of the proposed detection method in different situations,w ithout loss of generality,w e select four groups of data to compare the false negative and false positive rate of the proposed method w ith other detection methods show n in Tab.1,w hich use different combination of protocols and netw ork traffic rates,particularly the variation of traffic intensity in P2P programs.The 1st and 2nd samples are in the netw ork scenarios w ithout bot programs,and the 2nd and 4th samples contain a number of packets from P2P programs and other w eb applications.With the help of the method proposed in Ref.[27],the 3rd sample is acquired by merging the1st sample w ith the bot data captured from the netw ork scenarios show n in Fig.4,and the 4th sample is acquired by merging the 2nd sample w ith the bot data captured from the netw ork scenarios show n in Fig.4.The real attack times for the four groups of data are 0,0,1 000,and 1 000 in order.
| 图表编号 | XD0015629900 严禁用于非法目的 |
|---|---|
| 绘制时间 | 2018.06.01 |
| 作者 | 宋元章、陈媛、王俊杰、王安邦、李洪雨 |
| 绘制单位 | 中国科学院长春光学精密机械与物理研究所、中国科学院长春光学精密机械与物理研究所、中国科学院长春光学精密机械与物理研究所、中国科学院长春光学精密机械与物理研究所、中国科学院长春光学精密机械与物理研究所 |
| 更多格式 | 高清、无水印(增值服务) |